Overview
Microsoft Azure, commonly referred to as Azure, is a comprehensive cloud computing platform provided by Microsoft. It offers a wide range of services and tools for building, deploying, and managing applications and services through Microsoft’s global network of data centers.
Requirements for Microsoft Azure
Before adding the Azure account, you must create an application registration with commands. (source)
Info
The provided instructions are specific to Linux. It might look different with another Operating System.
1) If you haven’t installed Azure CLI, you can do it with the following command:
sudo apt install azure-cli -y2) Login
sudo apt-get install azure-cliYou will be redirected to an Azure page where you can choose your account:

CLI output will be similar to this:
[
{
"cloudName": "AzureCloud",
"id": "c0xxxxa5-xxx-4ecb-xxxx-f37bxxxx28d6",
"isDefault": true,
"name": "Bezplatná zkušební verze",
"state": "Enabled",
"tenantId": "32xxxxb3-xxx-46b3-xxxx-0exxxxc46d1",
"user": {
"name": "[email protected]",
"type": "user"
}
}
]You’ll need to fetch the Azure Subscription ID (“id”) and Azure Tenant ID (“tenantID”) fields from the output. Here’s what we would use in our test instance:
"id": "c0xxxxa5-xxx-4ecb-xxxx-f37bxxxx28d6”"tenantId": "32xxxxb3-xxx-46b3-xxxx-0exxxxc46d1"3) Create a new Azure App with the following command:
az ad app create --display-name kubernetes --identifier-uris http://kubernetes --homepage http://example.com --password CLIENT_SECRETYou’ll need to use your Client Secret in this command, which can be deleted later (e.g. “Ue9)Qj^V\~UYES3(C”)
CLI output will look like this:
{
"acceptMappedClaims": null,
"addIns": [],
"allowGuestsSignIn": null,
"allowPassthroughUsers": null,
! "appId": "7bxxxxc3-xxxx-4d74-xxxx-8c40xxxb558", !
"appLogoUrl": null,
"appPermissions": null,
"appRoles": [],
"applicationTemplateId": null,
"availableToOtherTenants": false,
"deletionTimestamp": null,
"displayName": "kubernetes",
"errorUrl": null,
"groupMembershipClaims": null,
"homepage": "http://example.com",
"identifierUris": [
"http://kubernetes"
],
}
...
{
"adminConsentDescription": "Allow the application to access kubernetes on behalf of the signed-in user.",
"adminConsentDisplayName": "Access kubernetes",
"id": "59xxx87-xxxx-47b8-xxxx-1708xxxxefcd",
"isEnabled": true,
"type": "User",
"userConsentDescription": "Allow the application to access kubernetes on your behalf.",
"userConsentDisplayName": "Access kubernetes",
"value": "user*impersonation"
}
...
}You’ll need to use the “appID” parameter from this output. In our example, it would be:
"appId": "7bxxxxc3-xxxx-4d74-xxxx-8c40xxxb558"
4) Create a service principal for the app:
az ad sp create --id appIdUse “appId” from the previous step here:
az ad sp create -id 7bxxxxc3-xxxx-4d74-xxxx-8c40xxxb558CLI output example:
{
"accountEnabled": true,
...
}
...
"objectId": "85xxxxcb-xxxx-4761-xxxx-63fxxxx515e",
"objectType": "ServicePrincipal",
"odata.metadata": "https://graph.windows.net/32xxxxb3-xxxx-46b3-xxxx-0e33xxxx46d1/$metadata#directoryObjects/@Element",
"odata.type": "Microsoft.DirectoryServices.ServicePrincipal",
}
...5) Create a role assignment:
az role assignment create --role "Owner" --assignee http://kubernetes --subscription SUBSCRIPTION_ID</code>In this case, you will use the subscription ID from step №2:
az role assignment create --role "Owner" --assignee http://kubernetes --subscription c0xxxxa5-xxx-4ecb-xxxx-f37bxxxx28d6You’ll find the following CLI output:
{
"canDelegate": null,
"id": "/subscriptions/c0xxxxa5-xxx-4ecb-xxxx-f37bxxxx28d6/providers/Microsoft.Authorization/roleAssignments/4fxxxx7f-xxxx-4ccf-xxxx-7287xxxxfa14",
"name": "4fxxxx7f-xxxx-4ccf-xxxx-7287xxxxfa14",
"principalId": "85xxxxcb-xxxx-4761-xxxx-63ffxxxx515e",
"principalType": "ServicePrincipal",
"roleDefinitionId": "/subscriptions/c0xxxxa5-xxx-4ecb-xxxx-f37bxxxx28d6/providers/Microsoft.Authorization/roleDefinitions/8exxxx57-xxxx-443c-xxxx-2fe8xxxxb635",
"scope": "/subscriptions/c0xxxxa5-xxx-4ecb-xxxx-f37bxxxx28d6",
"type": "Microsoft.Authorization/roleAssignments"
}Please be careful when inserting the credentials. If you add incorrect credentials, you cannot add flavor and create a cluster.
You can switch to Taikun and add your Azure credentials now:
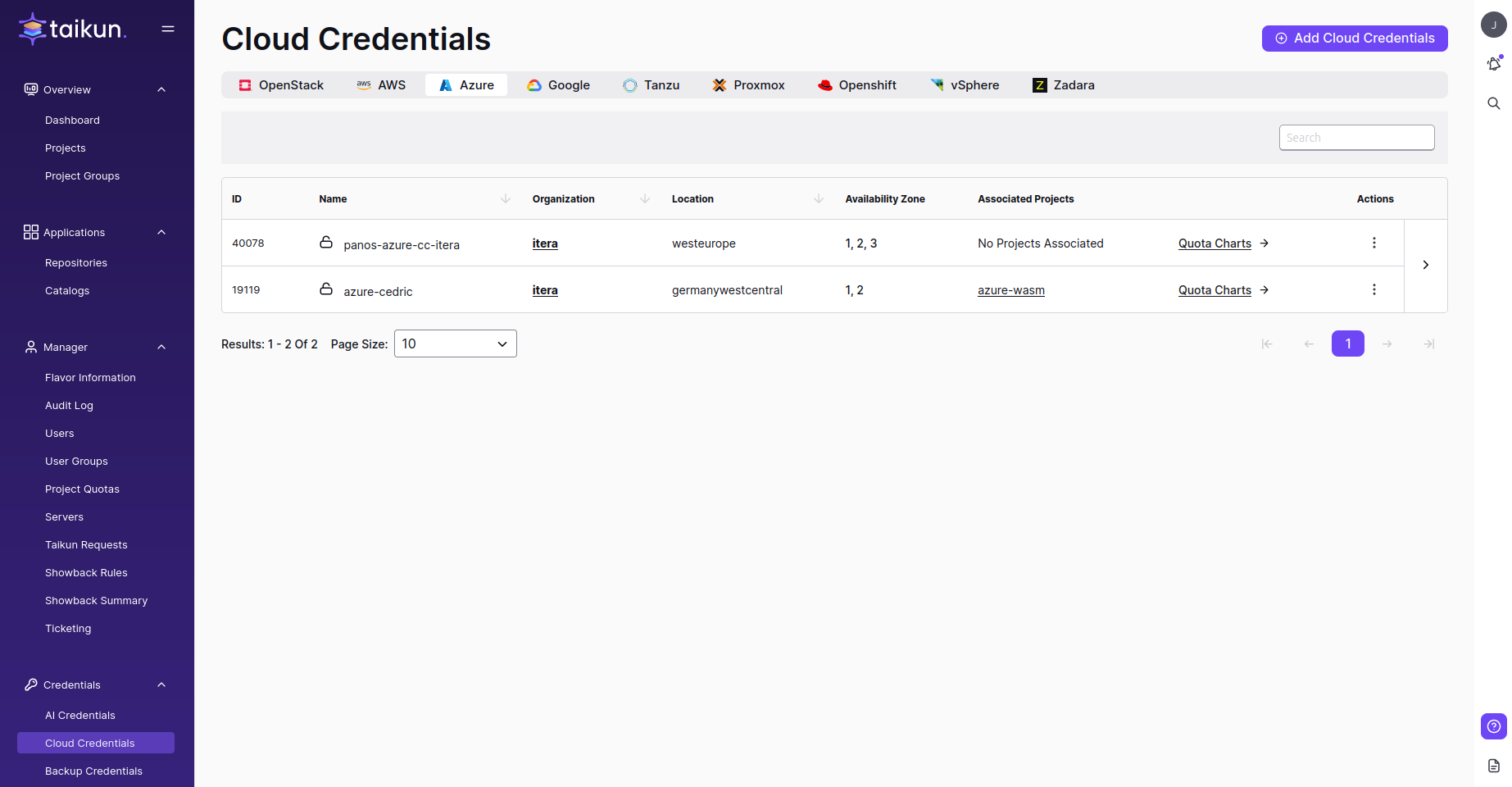

- Switch to Cloud credentials in Taikun
- Hit Add Cloud Credentials in the top-right corner
- Specify the necessary parameters in the Azure section:
- Cloud Name – choose a name for your Cloud Credentials (3-30 characters, e.g. cloud-test)
- Azure Client ID
- Azure Client Secret
- Azure Tenant ID
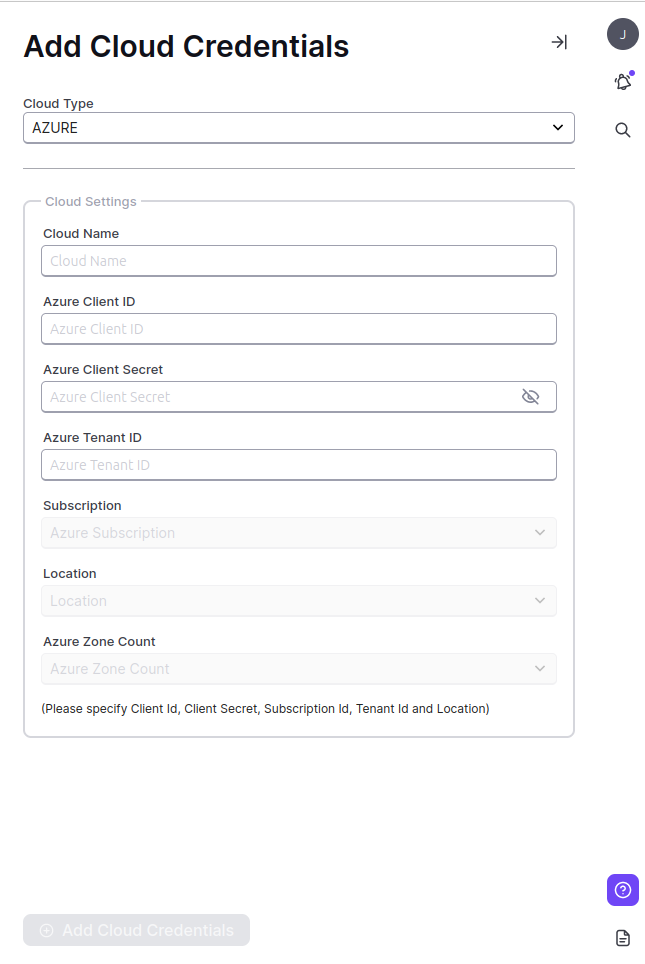

Where to find the Azure credentials
You can find the guidelines here if you haven’t created your application via CLI.
Credentials for Azure are located in different tabs. Instructions on where to find them are posted below.
Please be careful when inserting the credentials. If you add incorrect credentials, you cannot add flavor and create a cluster.
Azure Client and Tenant ID
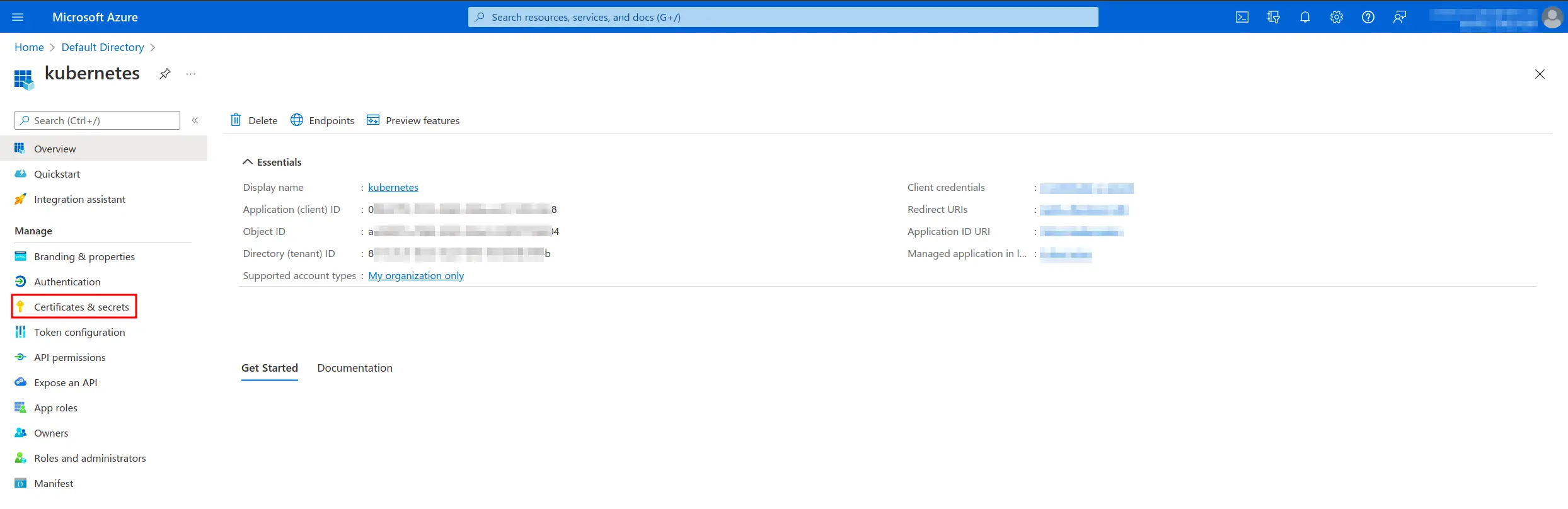
- Azure Active Directory – App registrations – All Applications – application -> Application (client) ID (=Azure Client Id) and Directory (tenant) ID (Azure Tenant Id)
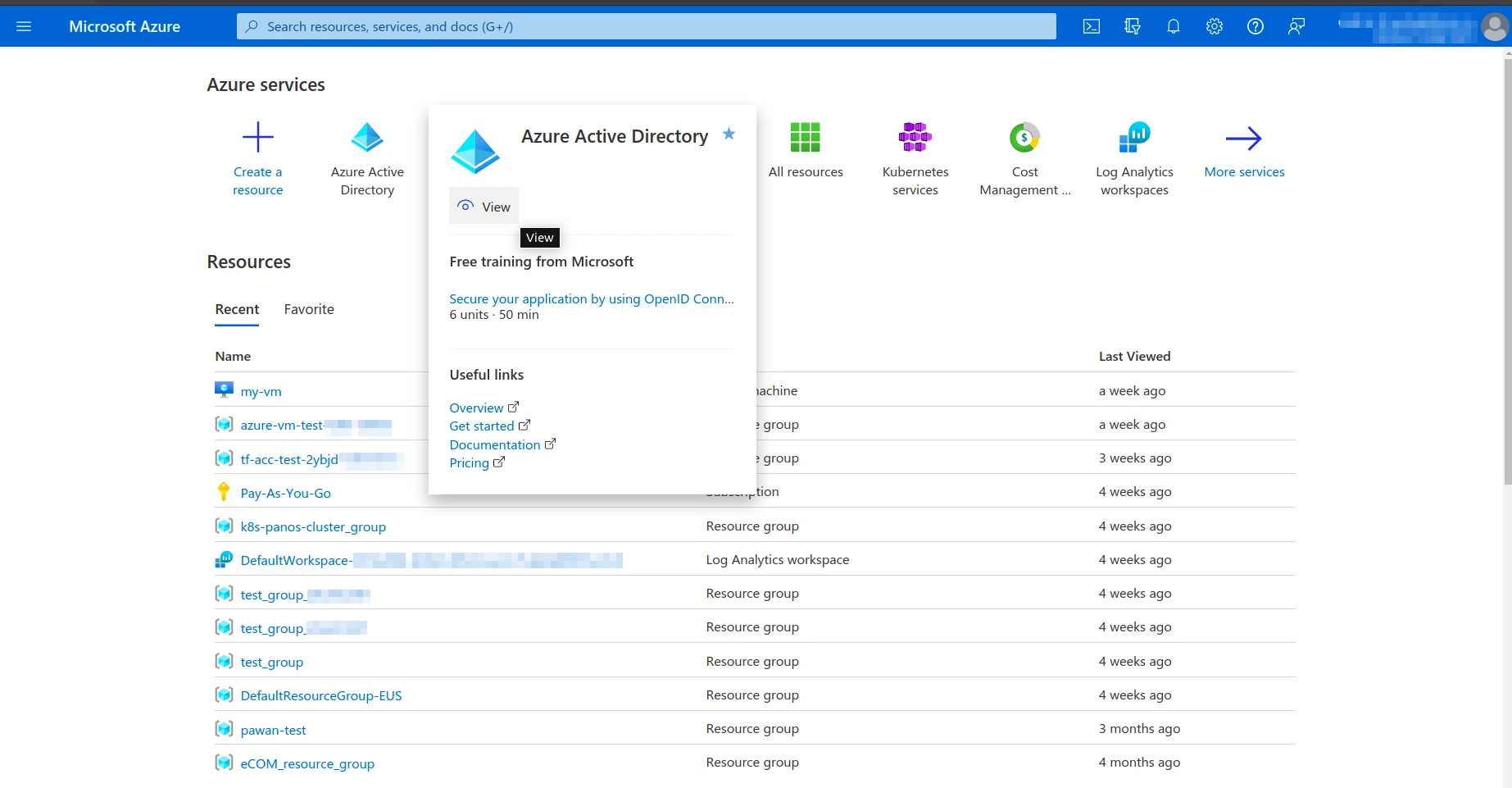


- Azure Active Directory – App registrations – All Applications – application – Certificates & secrets – Client secrets -> Value (=Azure Secret Id)



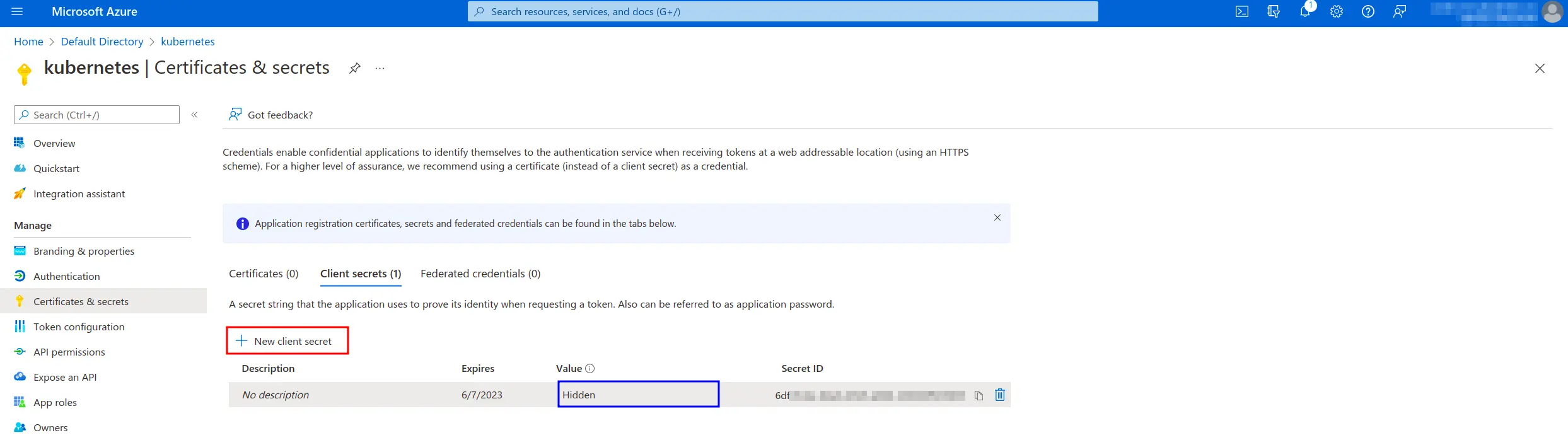

Warning
Client Secret is shown only for the first time, we recommend to save it somewhere else.
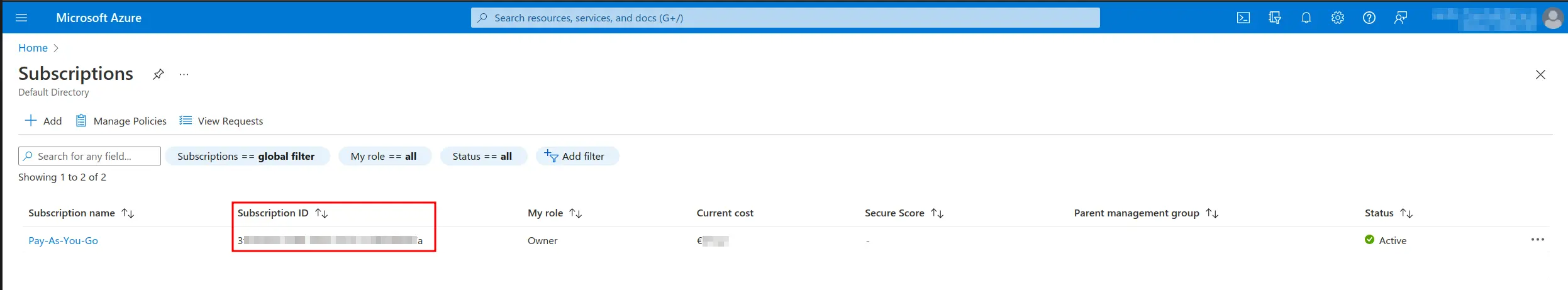
Azure Subscription Id
Note
Subscription is chosen from drop-down selection, but you can find below where to find your Subscription ID.
- Subscriptions -> Subscription ID (=Azure Subscription Id)


More information is provided in the Azure guideline


